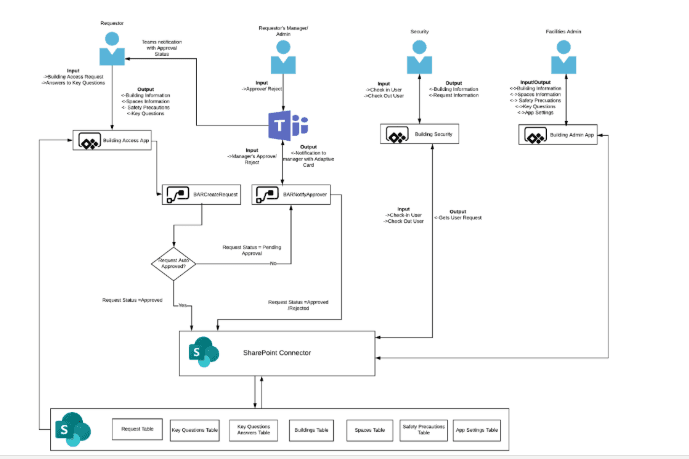
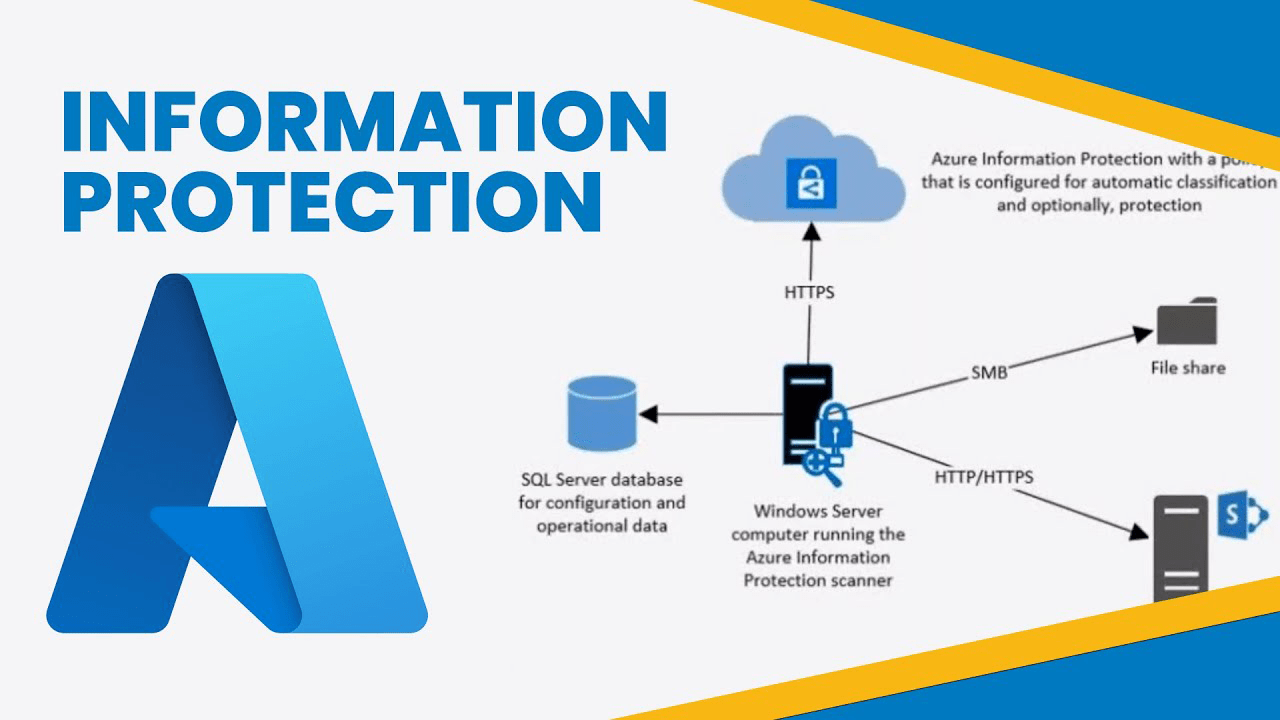
Trong thế giới an ninh mạng đầy biến động, việc bảo vệ các thông tin, dữ liệu hay còn được gọi là “tài sản kỹ thuật số” đòi hỏi nhân sự CNTT cần có sự hiểu biết sâu sắc về các rủi ro và cách thức phòng ngừa hiệu quả.
Việc bảo vệ an ninh mạng không chỉ đơn thuần là cập nhật phần mềm, triển khai hệ thống, dịch vụ tường lửa mà đòi hỏi cách tiếp cận toàn diện, đa chiều. Doanh nghiệp cần xây dựng chiến lược phòng thủ vững chắc dựa trên các nguyên tắc Zero Trust, xác thực đa yếu tố, kết hợp công nghệ tiên tiến với quy trình quản lý chặt chẽ và nâng cao nhận thức an ninh mạng cho người dùng. Hơn nữa, sự hợp tác, chia sẻ thông tin giữa các tổ chức, quốc gia là điều kiện then chốt để cùng nhau ứng phó với các mối đe dọa an ninh mạng ngày càng gia tăng.
Sự phát triển của công nghệ, đặc biệt là điện toán đám mây, IoT và trí tuệ nhân tạo, vừa mang lại cơ hội to lớn, vừa mở ra những kẽ hở bảo mật mới. Kẻ tấn công ngày càng tinh vi, sử dụng các kỹ thuật phức tạp như ransomware, phishing, tấn công DDoS, khai thác lỗ hổng zero-day để đánh cắp dữ liệu, phá hoại hệ thống, gây thiệt hại về tài chính và uy tín cho cá nhân, tổ chức, thậm chí là an ninh quốc gia.
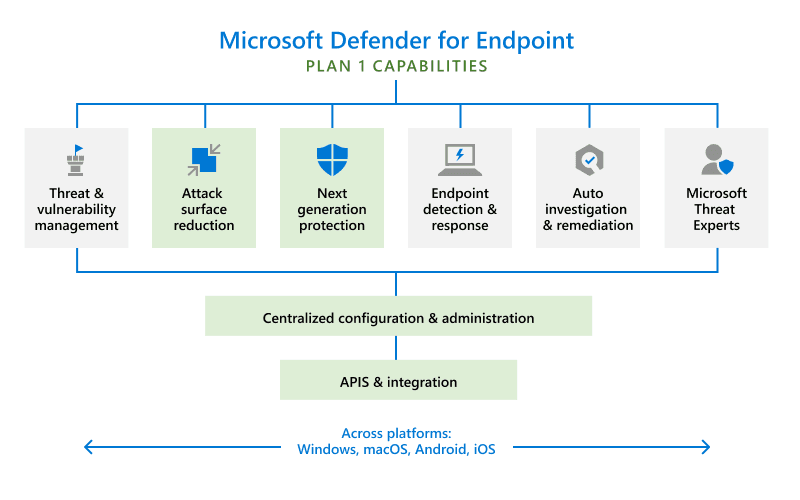
Ngày 25/05/2024 vừa qua hãng công nghệ Microsoft đã có bài viết nói về 10 định luật an ninh mạng cốt lõi, đóng vai trò như kim chỉ nam giúp bạn định hình chiến lược bảo mật vững chắc:
Immutable Laws of Security v1
- Security success is ruining the attacker’s ROI – Security can’t achieve a perfect secure state, so deter them by disrupting and degrading their Return on Investment (ROI). Increase the attacker’s cost and decrease the attacker’s return for your most important assets.
- Not keeping up is falling behind – Security is a continuous journey. You must keep moving forward because it will continually get cheaper for attackers to successfully take control of your assets. You must continually update your security patches, strategies, threat awareness, inventory, tooling, monitoring, permission models, platform coverage, and anything else that changes over time.
- Productivity always wins – If security isn’t easy for users, they work around it to get their job done. Always make sure solutions are secure and usable.
- Attackers don’t care – Attackers use any available method to get into your environment and access your assets, including networked printers, fish tank thermometers, cloud services, PCs, servers, Macs, or mobile devices. They influence or trick users, exploit configuration mistakes or insecure operational processes, or just ask for passwords in a phishing email. Your job is to understand and take away the easiest, cheapest, and most useful options, like anything that leads to administrative privileges across systems.
- Ruthless prioritization is a survival skill – Nobody has enough time and resources to eliminate all risks to all resources. Always start with what is most important to your organization or most interesting to attackers, and continuously update this prioritization.
- Cybersecurity is a team sport – Nobody can do it all, so always focus on the things that only you (or your organization) can do to protect your organization’s mission. If security vendors, cloud providers, or the community can do better or cheaper, have them do it.
- Your network isn’t as trustworthy as you think it is – A security strategy that relies on passwords and trusting any intranet device is only marginally better than lack of security strategy. Attackers easily evade these defenses, so the trust level of each device, user, and application must be proven and validated continuously, starting with a level of zero trust.
- Isolated networks aren’t automatically secure – While air-gapped networks can offer strong security when maintained correctly, successful examples are extremely rare because each node must be isolated from outside risk. If security is critical enough to place resources on an isolated network, you should invest in mitigations to address potential connectivity via methods such as USB media (for example, required for patches), bridges between the intranet network and external devices (for example, vendor laptops on a production line), and insider threats that could circumvent all technical controls.
- Encryption alone isn’t a data protection solution – Encryption protects against out-of-band attacks (for example, network packets, files, and storage), but data is only as secure as the decryption key (key strength + protections from theft/copying), and other authorized means of access.
- Technology doesn’t solve people and process problems – While machine learning, artificial intelligence, and other technologies offer amazing leaps forward in security (when applied correctly), cybersecurity is a human challenge, and will never be solved by technology alone.
Immutable Laws of Security v2
- Law #1: If a bad actor can persuade you to run their program on your computer, it’s not solely your computer anymore.
- Law #2: If a bad actor can alter the operating system on your computer, it’s not your computer anymore.
- Law #3: If a bad actor has unrestricted physical access to your computer, it’s not your computer anymore.
- Law #4: If you allow a bad actor to run active content in your website, it’s not your website anymore.
- Law #5: Weak passwords trump strong security.
- Law #6: A computer is only as secure as the administrator is trustworthy.
- Law #7: Encrypted data is only as secure as its decryption key.
- Law #8: An out-of-date antimalware scanner is only marginally better than no scanner at all.
- Law #9: Absolute anonymity isn’t practically achievable, either online or offline.
- Law #10: Technology isn’t a panacea.